The internet of things (IoT) is a digital technological revolution offering numerous advantages to the world of technology. Corporate firms, organizations, and enterprises will benefit from IoT implementation. IoT provides real-time business insight and data that effectively run an organization when implemented appropriately. However, it can be challenging to implement, especially when there is a knowledge gap or lack of technical know-how.
Tech-related professionals such as developers, architects, IT administrators, and CIOs interested in IoT deployment must thoroughly understand the concept of IoT. To get the best out of it, they must know what IoT is, its functions, how it operates, its requirements, benefits, trade-offs, and how its infrastructures and devices must be implemented. It is also essential to understand that IoT is still in its early stages; therefore, it is an innovation with huge potential.
Although it is still in its early stages, IoT implementation is more significant than the industrial revolution. IoT will be a market disruptor, giving tech-related professionals and early adopters a competitive edge like previous revolutions. This would help many organizations adapt or create their business around new technologies and challenge even old competitors in their industry.
IoT Implementation Requirements
Specific tools are required to implement IoT successfully. The industrial IoT requirements are:
Cloud Computing
Cloud computing ensures that structured and unstructured information is processed and stored in real-time data.
High-level Security
An essential IoT requirement is high-level security. It ensures that sensitive information remains confidential.
Accessibility
Accessibility is an IoT requirement that enables authorized users to access IoT devices anytime in any location.
Reliable Data Analytics
An ideal requirement for IoT processes is reliable data analytics. This provides intelligent information during industrial processes.
Asset Management
With proper asset management, IoT systems will function appropriately. It will also be better maintained if managed through cloud-based services.
Seamless User Experience
A user-friendly interface can create a better user experience. This also improves the adoption of IoT systems.
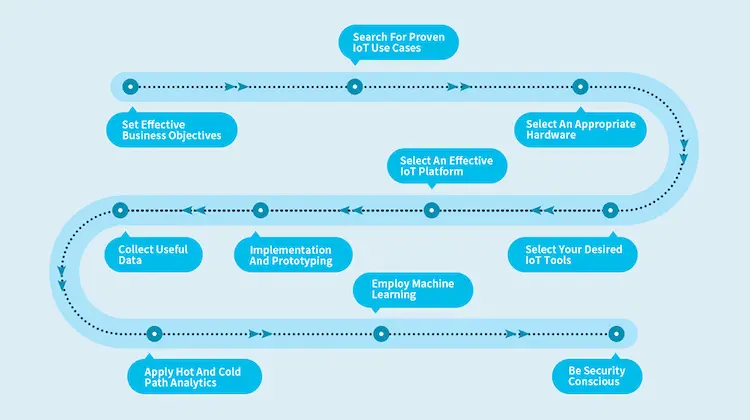
Steps For IoT Implementation
There are always high expectations for IoT projects. An organization may afford the human resources and technical tools but could still fail without the appropriate steps for IoT implementation. Therefore, it is essential to know what IoT implementation is for and how to implement IoT systems.
This way, it will improve your business and meet all expectations. It would also cause higher cost-efficiency and enhance your existing services by creating new possibilities or adding extra features. For successful IoT Implementation, here are the basic steps to follow.
Step 1: Set Effective Business Objectives
Successful IoT implementation involves setting practical business objectives. You can employ the services of IoT specialists or engineers if you lack the know-how. This will help you decide if IoT requires investments for a short or long period. You will also figure out if the investment will yield tangible returns. When setting your business objectives, clearly define your goals for IoT. You must understand and state:
• The problem in the short and long term
• The aim for solving the problem
• The best way to solve the problem
Step 2: Search For Proven IoT Use Cases
Although IoT is relatively new, it has existed long enough to be developed in several areas. Also, several organizations have adopted IoT devices, causing them to become more famous. Therefore, an essential step to effective IoT implementation is researching proven use cases. This would help you identify the loopholes in your business objectives and plans with IoT implementation. Some of the common tested use cases of IoT you can research include:
• Preventive Maintenance
• Automatic Refilling
• Resource Micromanagement
• Asset Tracking And Management
• Environmental Monitoring
• Design for IoT
• Access Control And Security
• Process Control And Optimization
Step 3: Select An Appropriate Hardware
When you decide to adopt IoT implementation, you need to determine the factors involved. Understanding every IoT asset or device to be integrated into the network is essential. Ensure you select appropriate hardware consisting of the most primary sensors. Examples of the devices used for accurate data collection include volume, weight, color, sound, vision, temperature, pressure, and humidity. You will need to upload the data on the cloud with another hardware.
A connection device is a hardware used to connect the data-gathering sensor and other devices to the IoT network. The other devices, such as actuators and edge computers, depend on the target to be achieved. 6LoWPAN, Zigbee, and Z-wave are new protocols specifically designed for implementing IoT. However, not every device is compatible with all protocols.
Step 4: Select Your Desired IoT Tools
The internet plays a pivotal role in successful IoT implementation; therefore, you must have a strong internet speed. However, the IoT devices you select determine their effectiveness. You connect an IoT device to the internet for several reasons, such as:
• Collecting, processing, and sending sensor data to designated endpoints
• Receive commands to set or do tasks and control actuators
Several IoT-oriented devices can be designed to work with the user’s habits. They can help predict the user’s wishes and notify them of any problems. Such devices include smart thermostats and appliances, IP cameras, drones, and voice controllers.
Step 5: Select An Effective IoT Platform
IoT platforms are software for centralizing and controlling all aspects of IoT devices and networks. You can get these IoT platforms from specialized suppliers or custom-made in-house. Once you get an effective IoT platform, it becomes the foundation of the network–everything else is built around it.
Step 6: Implementation And Prototyping
Before implementation, you should assemble a team of several tech professionals. The team should then thoroughly analyze the entire process. This is because many systems interact with each other during IoT processes.
Some of the experts to include in the team consists of IT experts, telecommunications specialists, manufacturing experts, computer, software, electronic, mechanical, mechatronics, and automation engineers. The experts selected depend on your target for IoT. Once your team has been assembled, design your implementation and test the prototype.
Step 7: Collect Useful Data
A crucial step for implementing IoT is collecting sufficient and valuable data. Several sensors can be used for this; however, more complex needs would require more sensors for data collection. Some of the standard sensors include oil, integrity, and fuel sensors. You may also be generating terabytes of data daily. The data generated must be interpreted, processed, and stored on a secure database.
Step 8: Apply Hot And Cold Path Analytics
Hot or cold path analytics are decision-making processes. Hot path analytics are short-term, while cold path analytics focuses on the long-term. They involve storing the data collected by the sensors in parts or wholly. The data is converted or interpreted by embedded systems and later analyzed.
You can depict your systems, resources, production, present data, and assets’ status over time with the available information. Hot and cold path analytics are analyses performed by data scientists, aided by machine learning software. It enables businesses to figure out needed changes for better efficiency. Stored data can be analyzed and re-analyzed severally for safety measures.
Step 9: Employ Machine Learning
Machine learning involves using artificial intelligence to review information in real-time. It helps to identify patterns in the data and act on them. Artificial intelligence performs data analysis to understand historical occurrences, predict human behavior, the need for maintenance, among others. This helps to identify patterns in the data. Artificial intelligence would supplement data scientists or eventually replace them.
Step 10: Be Security Conscious
Being security conscious is one of the ways to protect your business from unforeseen attacks. Many organizations have lost or been forced to pay top dollars because of poor security measures. Ensure you deploy effective security measures that can protect your business from hacking and other attacks.
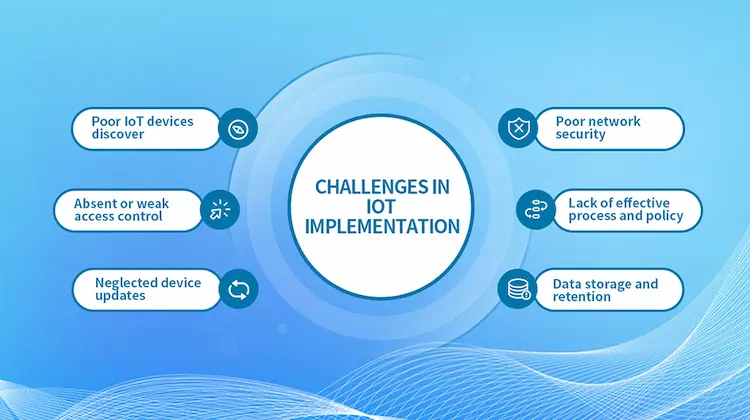
Challenges In IoT Implementation And Solutions
IoT is faced with several challenges that need to be resolved before its full potential can be attained. Although IoT Implementation challenges and risks are primarily understood, IoT devices’ absolute diversity and the application still require a higher level of control and attention than most businesses may exercise. If these IoT challenges are resolved, IoT implementation would be unstoppable. Here are some of the most
detrimental risks and challenges of IoT environments
Poor IoT Device Discover
A significant challenge in IoT Implementation is the lack of adequate discovery of IoT devices. This is a challenge because undiscovered devices can’t be managed, becoming attack vectors for fraudsters and hackers to access the network efficiently. To resolve this challenge, the admins must be equipped with tools to discover and control all IoT implementation devices on their network. They must also ensure that all IoT tools and practices can configure all IoT devices within the environment.
Absent Or Weak Access Control
Another challenge in IoT implementation is absent or weak access control of IoT devices and products. IoT security depends heavily on the authentication and authorization protocol of each device. This strengthens the network’s security measures. Having a unique identifier for each device would go a long way to enhance access control.
However, configuring each IoT device and product for the least privilege is key to having the best access control. This would ensure that unauthorized users can only access the public resources on the network, while the essential and private resources are limited to only authorized users. Other security measures such as enabling network encryption and strong passwords can also be adopted and enforced for every IoT device.
Neglected Device Updates
Neglected device updates are a significant IoT implementation challenge that needs to be resolved. Periodically, IoT devices may require patches or updates to internal firmware and other software. IoT devices could be susceptible to hacking and intrusion if these updates are overlooked or neglected.
Therefore, the admins need to run regular updates on all IoT devices for effective and efficient IoT implementation. The updated logistics and desired practice should be considered when designing the IoT environment. Sometimes, it may be impossible or difficult to update some devices in the field. These devices may also be difficult or inaccessible to take offline. In such cases, an effective solution should be deployed.
Poor Network Security
Security is a significant concern for any innovation, irrespective of its application. For innovation to thrive, it must be secure or have efficient means for its security. Sadly, IoT devices suffer from poor network security. IoT deployments regularly add thousands of devices, which are all connected to a LAN. With every device connected to the LAN, a potential access point for hacking or intrusion is opened.
An additional network-wide security protocol must be deployed to implement IoT effectively. This could include intrusion prevention and detection systems, powerful antimalware tools, and tightly controlled firewalls. The IoT network might also be segmented from other IT networks. With this level of security in place, the network would be better secure.
Lack Of Effective Process And Policy
Process and policy are essential for adequate network security. Security process and policy represent the combination of effective practices and tools used for configuring, enforcing, and monitoring IoT device security throughout the network. However, it remains one of the risks and challenges affecting IoT implementation. These IoT challenges can affect a business severely; therefore, before any IoT project is deployed, they must be recognized and appropriately considered.
Everyday IoT security processes and policies must be recognized to solve the lack of effective policies. Clear configuration guidelines, proper documentation, rapid response, and reporting are examples of IoT security processes. IoT implementation would be significantly improved if these processes could be implemented adequately. This would, therefore, comply with businesses irrespective of the deployment scope employed.
Data Storage And Retention
Another severe challenge of IoT implementation is data storage and retention. A significant amount of data is produced by a single IoT device. It would be enormous when all data produced is multiplied by the number of devices involved. The data produced by IoT devices is a valuable asset.
Therefore, better tools must be provided to appropriately store and secure these data. However, many businesses lack the capacity or struggle to keep such enormous data effectively. The data stored is highly time-sensitive, as IoT data possess a different lifecycle compared to traditional business data. It could be referenced to or needed for delicate business dealings in decades to come, and if not well stored, could affect the business.
Choose Mokosmart IoT Solutions
MokoSmart is a popular and highly-rated professional hardware manufacturer offering the best IoT solutions in the market. We are dedicated to the research, manufacturing, and development of smart devices. We work with organizations in the electronic engineering, white-label solution, firmware customized, and wholesale program industry.
We also specialize in designing and manufacturing quality IoT hardware, offering a range of products and programs globally for the smart device market. Our IoT Implementation examples include smart switches and sockets, Bluetooth modules, beacons, wireless sensors, and LoRa®-Based products. When you choose MokoSmart, you are guaranteed reliable and top-quality IoT solutions.